On Monday, 28 March, Nandan Kumar, a software engineer from Bengaluru, wrote a series of tweets claiming to have discovered a "technical vulnerability" in IndiGo airline's website, which "leaks sensitive data".
After flying from Patna to Bengaluru he ended up going home with another passenger's bag, "Honest mistake from both our end. As the bags are exactly the same with some minor differences."
He contacted IndiGo to get his luggage back, but "couldn’t get any resolution" on the issue. The airline didn't provide him with the contact details of the co-passenger who had his bag, citing privacy concerns.
Kumar, armed with the co-passenger's PNR and last name, says he then opened the developer console on the website and was able to retrieve the latter's phone number and email ID through a "hole" in the system.
In most cases, however, you don't even need to dig around in the website's source code if you want to find personal details. If you have someone's PNR and last name, their information is usually visible on the website itself.
‘My Low-key Hacker Moment'
If you have access to someone's PNR and last name, you can usually gain access to their itinerary, which has their contact details. We tested this with three IndiGo travellers and were able to access their addresses, phone numbers, and emails.
We were also able to access the phone number and email of an Air India passenger using their PNR and last name.
"Any passenger can retrieve their booking details using PNR, last name, contact number, or email address from the website. This is the norm practiced across all airline systems globally," said IndiGo in a statement.
However, Kumar's case seems to be an anomaly. Even though he had the PNR and last name, his co-passenger's contact details were not available on IndiGo's itinerary page. The Quint has independently verified this.
We asked IndiGo what the criteria to determine whose details are available on the website is, but we haven't received an answer.
After realising the bag wasn't his, Kumar says he called customer care who tried to connect him with the co-passenger, but to no avail. He then tried accessing the co-passenger's itinerary, which also didn't work.
"After all the failed attempts, my developer instinct kicked in and I pressed the F12 button on my computer keyboard," he wrote.
Here's how he accessed his co passenger's contact details:
He went into the developers console in his browser while on the edit booking page on IndiGo's website.
He opened the network log, which records the activity on the webpage, and then logged in using the PNR and last name he found on his co-passenger's bag.
There was a file in the network log that contained the co-passenger's contact details and his address. This means that the page had accessed the information even though it wasn't displaying it.
Kumar used the information to get in touch with the co-passenger and get his luggage back.
IndiGo said that it is reviewing this case in detail and that its IT processes are "completely robust and, at no point was the IndiGo website compromised."
"Our customer care team followed protocol by not sharing any other passenger’s contact details with another passenger. This is in line with our data privacy policies. Attempts were made by the customer care team to facilitate the exchange of baggage, but it could not be completed as the calls went unanswered," it said in a statement.
If You Advertise Your PNR, You’re Open To Doxxing
This incident highlights how easy it is for someone to get hands on your phone number, email ID, and address. People can also gain access to details about your family, your food preferences, and your travel plans.
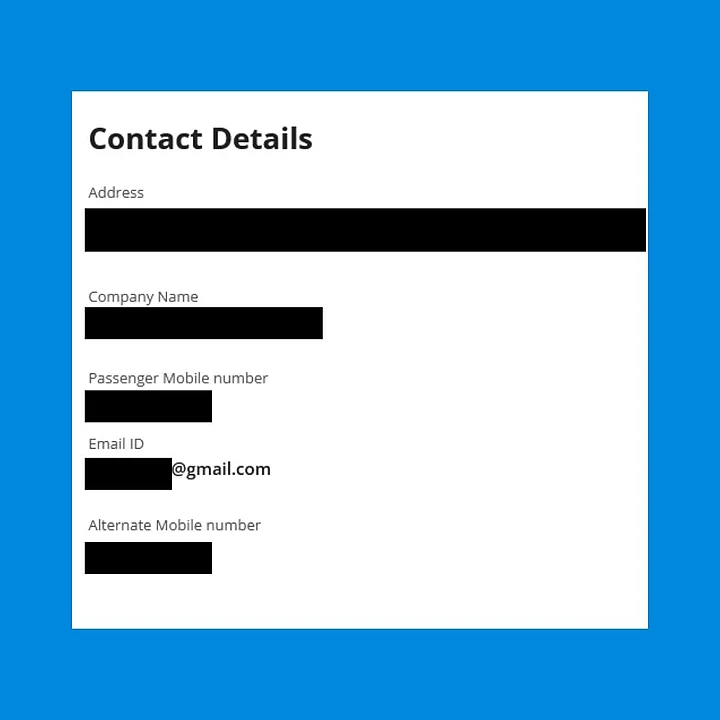
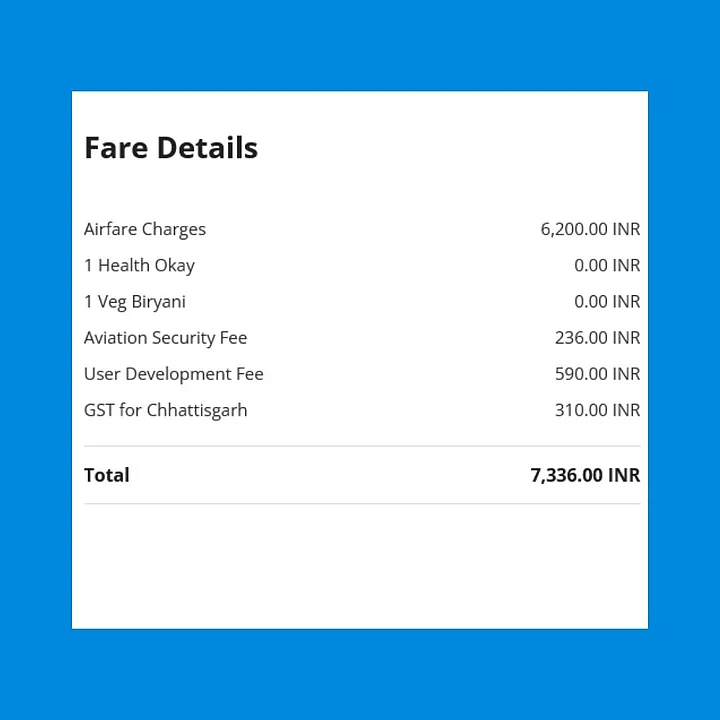
For instance, here's what we found when we retrieved details for a photograph of a boarding pass posted on social media:
The address, the name of their company, their email ID, two separate mobile numbers, the amount they spent on their ticket, and their preference for vegetarian food.
- 01/03
A boarding pass posted on social media.
(Photo: altered by The Quint)

- 02/03
Contact details.
(Photo: altered by The Quint)

- 03/03
Fare details.
(Photo: altered by The Quint)

We found dozens of such boarding passes floating around on social media. If you have ever posted a photo of your boarding pass or ticket online, you might be vulnerable to doxxing.
Doxxing involves looking up the details of people’s lives, usually by digging through their social media profiles, publicly available data, government records, and even comments across old and defunct message boards.
While snippets of this information might be irrelevant individually, put together, they can cause real harm. Some one can use this to threaten, harass, or stalk you.
Access to your PNR and last name also means that someone, malicious enough, could tamper with your booking schedule or even cancel your flight.
(At The Quint, we question everything. Play an active role in shaping our journalism by becoming a member today.)