(This is Part-II of an investigative series on how money meant for small and marginal farmers under the PM KISAN scheme was diverted to accounts opened using publicly available Aadhaar numbers. You can read Part-I here)
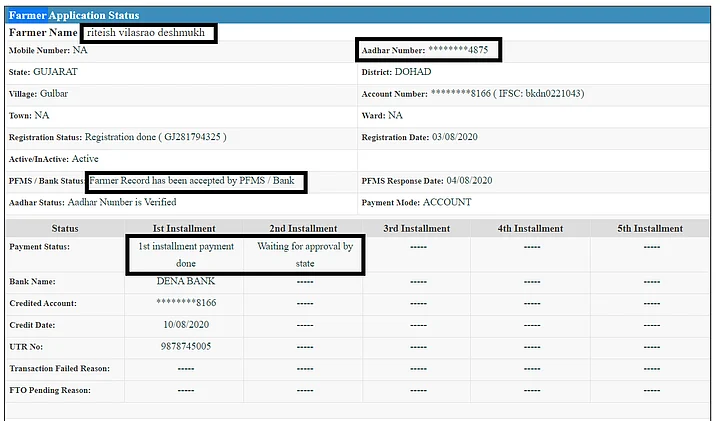
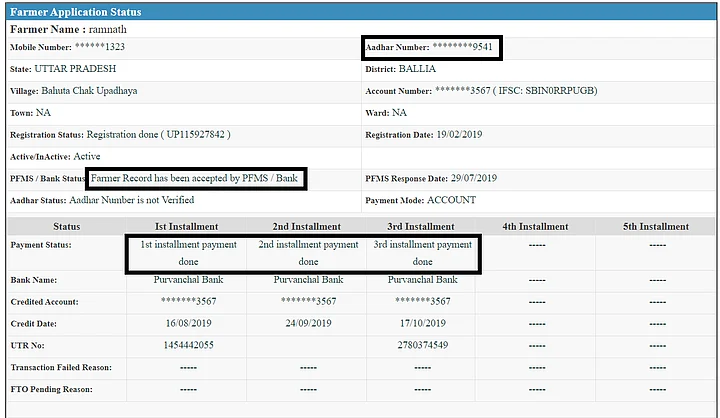
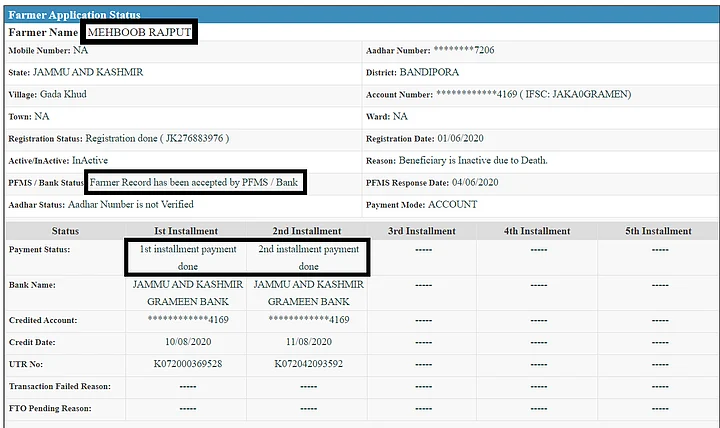
The Quint, in an exclusive report on Thursday, 10 December, showed how accounts created with publicly available Aadhaar cards belonging to actor Riteish Deshmukh, Lord Hanuman and ISI spy Mehboob Akhtar were used to sign up for the PM KISAN scheme and even receive cash meant for small and marginal farmers.
As per records of the Centre’s PM-KISAN scheme, Deshmukh, Lord Hanuman and Mehboob are all “small and marginal farmers” eligible for social security. Each of them has also received Direct Benefit Transfer (DBT) instalments of Rs 6,000, Rs 4,000 and Rs 2,000 respectively.
According to payment records accessed by The Quint, scamsters successfully registered for the scheme on the PM-KISAN portal using publicly available Aadhaar numbers of the above mentioned persons, a bank account number, land record details and a phone number.
This data was accepted by the official Public Financial Management System (PFMS) software, thereby making them eligible to receive DBT of Rs 2,000 per instalment, up to Rs 6,000 a year.
While a valid Aadhaar number was issued in the name of Lord Hanuman in 2015, ejected Pakistan High Commission official Mehboob Akhtar was found with a valid Aadhaar as “Mehboob Rajpoot” in 2016.
Experts tracking DBT programs told The Quint this scam using publicly known Aadhaar numbers is likely to be happening at a much larger scale given over 10 crore beneficiaries are registered with the scheme.
Tamil Nadu alone has been found to have at least 5.5 lakh ineligible beneficiaries in a recent government probe resulting in a loss of Rs 110 crore to the exchequer.
Following a probe initiated under the orders of Assam Chief Minister Sarbananda Sonowal, field officials said they were able to identify 9,000 ineligible persons on the beneficiary list from a single district – Lakhimpur.
The Quint investigated how Aadhaar numbers available in the public domain were used to open bank accounts or link existing accounts and sign up for the PM-KISAN scheme. Here’s a step-by-step explanation of the modus operandi.
The Modus Operandi
PM Kisan Samman Nidhi or PM-KISAN is a central sector scheme, 100 percent funded by the Government of India. It was operationalised on 1 February 2019 and provides an income support of Rs 6,000 per year in three equal instalments to small and marginal farmer families having combined land holding/ownership of up to 2 hectares.
According to a reply in the Lok Sabha by Union Agriculture Minister Narendra Singh Tomar on 9 September, a total amount of Rs 94,119 crore has been disbursed to 10.21 crore beneficiaries across the country under the scheme thus far.
The manner in which the scam was carried out follows a straightforward procedure as explained below.
Dr Subhashis Banerjee, professor of computer science at IIT-Delhi who has also worked on offline Aadhaar verification, says that the issue reveals “a failure at the level of the bank, PM-KISAN, the PFMS software as well as UIDAI for failing to communicate its offline use properly to banks.”
I. ACQUIRING PUBLICLY AVAILABLE AADHAAR CARD
First, the scamsters search for publicly available Aadhaar numbers and the corresponding JPEG/PDF images, so that they can take a print out and make a laminate, thus creating the “Aadhaar card”.
The Aadhaar numbers of all three – Deshmukh, Hanuman and Mehboob – are publicly available.
II. AADHAAR-BANK ACCOUNT LINKING
Second, they then use the card to create a new bank account that matches the given name in the Aadhaar card.
With the Supreme Court disallowing Aadhaar-based eKYC by banks, QR code-based offline verification is what banks could’ve done to match the applicant with the name and photo associated with the Aadhar number.
While Deshmukh’s Aadhaar has been linked to a Dena Bank account in Gujarat, Hanuman’s Aadhaar has been seeded with a Purvanchal Bank account in UP and Mehboob’s with J&K Grameen Bank.
Dr Banerjee told The Quint that in the offline process the bank could’ve used the QR code verification and easily found the mismatch in the Aadhaar number holder and the person at the bank.
“The offline design would have the QR code with all the Aadhaar information of the person including a photograph and the digital signature of UIDAI which are untamperable,” Dr Banerjee said adding “anyone who cans the QR code, will get the details and declare that the match has happened. If the match doesn’t happen it will have to be recorded as such.”
Srikanth Lakshmanan, an engineer and researcher tracking DBT schemes, adds a new account may not have been opened in each case. “Existing accounts that were previously not linked to Aadhaar could also have been linked with these publicly available Aadhaar numbers without the requisite authentication process,” Lakshmanan said.
III. REGISTERING FOR PM-KISAN SCHEME
Third, using these details, Aadhaar number and Aadhaar seeded banked accounts, along with some land details, they then register to become a farmer in the PM-KISAN portal. The Portal asks for land record details, Aadhaar number, bank information and a phone number.
IV. RECEIVING CASH
Fourth, if approved by the PFMS, they are then eligible for receiving Direct Benefit Transfers of INR 2,000 per instalment.
While the account under the name and Aadhaar of Riteish Deshmukh received one instalment of Rs 2,000, the account seeded with Hanuman’s account received Rs 6,000 and Mehboob got Rs 4,000.
Independent security researcher Srinivas Kodali says rigorous field verification is vital in such cases “as there are Aadhaar numbers from other states that are being used in a different state to claim DBT benefits with details of real people but who are not living anymore in the location of welfare distribution.”
Aadhaar Numbers Available Far Too Easily
While in Tamil Nadu, government officials had allegedly provided passwords to the beneficiary databases for ineligible names to be added to the list, The Quint has now found evidence of scamsters using Aadhaar numbers available publicly to enrol under names of the Aadhaar holders.
In September 2018, The Quint had also highlighted the ease with which Aadhaar numbers could be accessed publicly on Google image search. In a major breach of privacy, entities of various kinds that demand Aadhaar as proof of identity, have kept their entire directories open and publicly searchable on Google.
Scanned copies of Aadhaar cards are peppered in the search results that come up when one Googles “aadhar.jpg” or “aadhaar.jpg”.
In the case of each of the four individuals mentioned earlier, their Aadhaar numbers have been publicly available.
The Why & How: Systemic Vulnerabilities at Scale
What allows this modus operandi to thrive at a big scale are systemic vulnerabilities that have crept in at various parts of the loan dispersal mechanism.
For instance, the UIDAI has always said that with just the Aadhaar card and the demographic information, no harm can fall upon the holder (even though the law forbids displaying it in public). This stand aids the scamsters to create an impersonation attack by creating the “Laminated card” picked up from the public domain.
“If your payment system is through Aadhaar, then you cannot open a bank account with Aadhaar because that opens up a ground for fraud,” said Prof Banerjee.
While the UIDAI has insisted earlier that without biometric/OTP authentication, the number or card itself can’t be used to create any harm or financial fraud, Srinivas Kodali, an independent security researcher, says verifying Aadhaar has become a complicated process.
“eKYC allowed verification of people with biometrics. But with Supreme Court restricting Aadhaar bank linking, banks don't have access to it. Only the new modes of offline Aadhaar with photo QR codes and Aadhaar PVC cards with hologram can help with absolute verification,” Kodali told The Quint.
“If UIDAI has developed offline Aadhaar using QR code, why has this not been communicated to banks,” asks Dr Banerjee. “These verification protocols – that the card itself has no meaning and that the QR code on the card has to be machine read – was just not communicated properly.”
It’s a weak protocol that can be strengthened effortlessly. The Photo in the QR code is signed digitally by UIDAI, and if tampered with will not work. The digital signature establishes authority.
Finally the PFMS only verifies if the Aadhaar number is valid and the demographic information submitted by the Applicant matches with the information in the Aadhaar database and with the bank account. But even this is done only in 5 percent of the cases on a year-on-year basis as the reply from the Agriculture Minister Narendra Tomar indicates.
Put together, these loopholes caused systemic vulnerabilities that are exploitable at scale and indicate that the promise of the Direct Benefit transfer, that it would only help genuine farmers and not scamsters, is now on a shaky ground.
(At The Quint, we question everything. Play an active role in shaping our journalism by becoming a member today.)